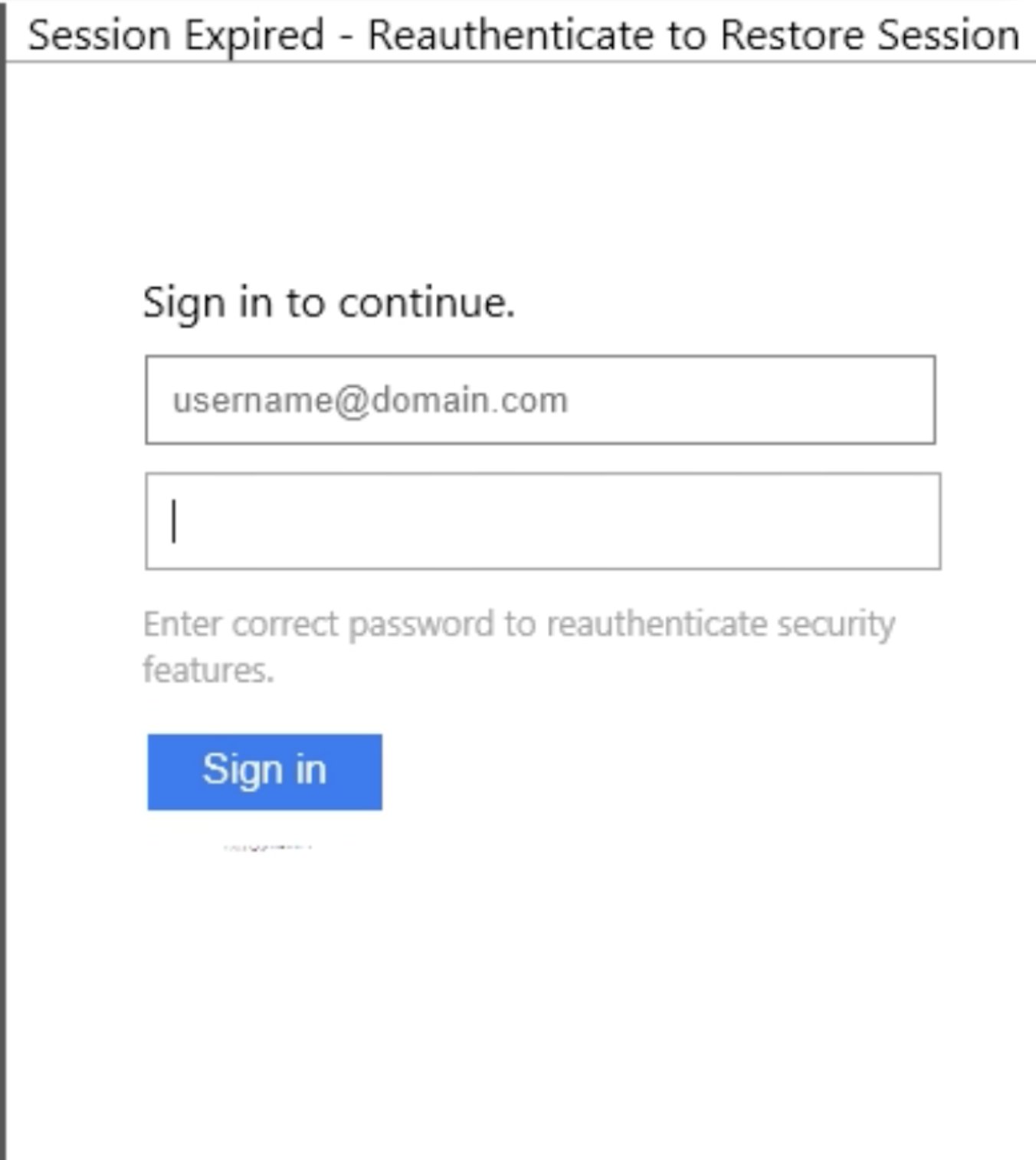
VT: 0/58 MB: 0/8 Filename: pl2auth.html MD5:1ce0a94c569efcaffb106b5624820030 IOCs: https[:]//sendargo[.]sbs/loqs/play/one/send[.]php https[:]//iprisky[.]sbs/mx2.2/?access= Report: Click here
Author Archives: docguard
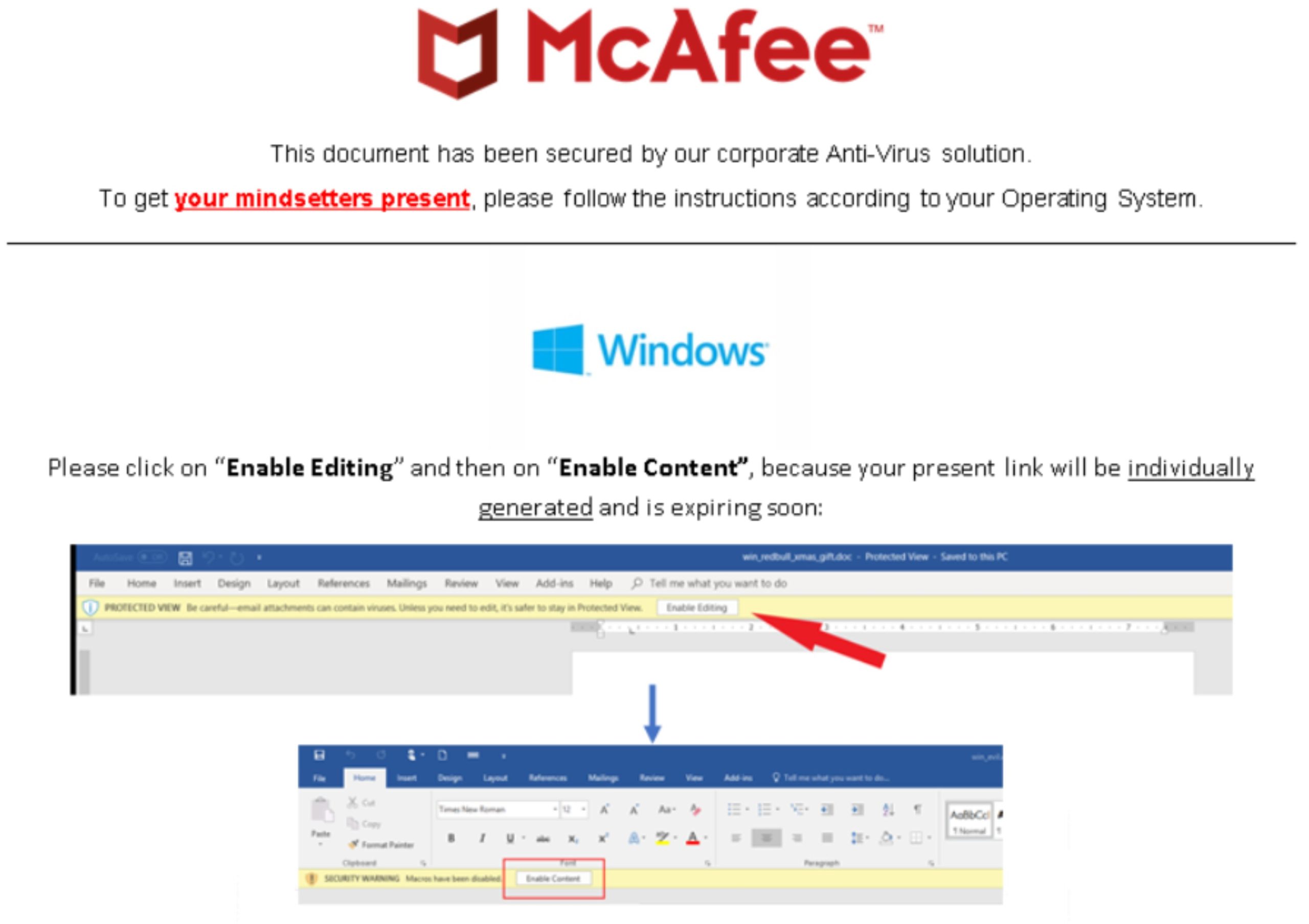
Social Engineering Test Evaded Nearly all the AVs
VT: 1/61 Filename:mindsetters_present1.doc MD5:4d5d951f2033e7e926395e8e0f7de847 IOCs: http[:]//ec2-34-255-85-35.eu-west-1.compute.amazonaws.com/api/rbuser Report: Click here

Rise of OneNote Documents for Phishing Attacks
OneNote is a digital notebook created by Microsoft that can be used through Microsoft 365product suite. Security researchers have discovered that attackers are using Microsoft OneNoteto deliver malware. OneNote has been used to steal data and provide remote access to … Read More
Royal Road is still in use!!
Recently, DOCGuard has identified several RTF samples uploaded to our cloud. Upon further investigation, it has been determined that these samples are associated with the RoyalRoad tool. Royal Road tool: RoyalRoad is a highly sophisticated hacking tool that has been … Read More
In-Depth Analysis of Typhon Stealer
DOCGuard Research team identified a new sample of stealer malware called Typhon Stealer, which has a list of capabilities to steal information from systems. In the first version of Typhon stealer, based on a source code of StormKitty stealer malware … Read More
LockBit3.0 Manual Analysis
LockBit 3.0 (also known as LockBit Black) is a strain of ransomware borne from the LockBit ransomware family. This is a group of ransomware programs that was first discovered in September 2019, after the first wave of attacks took place. … Read More
LNK file-based Attacks Are on The Rise
Introduction After Microsoft disabled the macros in Microsoft Office, criminals started to look for new techniques to beat security defenses and make it harder to detect malware and hide it from security solutions. LNK attack is one of the powerful … Read More
#APT Attack Targeting Russia
Today, we identified a sample uploaded to DOCGuard that targets Russia. This file uses template injection to connect to C2 and download the next stage. What is a template injection? Microsoft Word has a feature where a user can create … Read More

Running Shellcode Through Windows Callbacks Using VBA Macro
87% of the ransomware found on the dark web has been delivered via malicious macros to infect targeted systems. Because of this reason, AV and Sandbox vendors try to extend their Macro detection capabilities. On the other hand, attackers have … Read More
What is VBA Stomping?
Threat actors employ a variety of strategies to conceal dangerous macros; VBA Stomping is a brilliant trick for embedding macros in Office documents (e.g., a .xlsm Excel workbook) in a way that can deceive security tools. At this point, Docguard … Read More