Threat actors employ a variety of strategies to conceal dangerous macros; VBA Stomping is a brilliant trick for embedding macros in Office documents (e.g., a .xlsm Excel workbook) in a way that can deceive security tools.
At this point, Docguard has brought a unique perspective to static analysis, and the organization called this approach “Structural analysis.” And Docguard can easily detect VBA stomping vector using its unique structural analysis engine.
What can a malicious VBA Macro do?
Since VBA communicates directly with the win32 API (direct call), it can take any action that the attacker can direct on the operating system.
Therefore it is possible to write malware entirely in VBA. But in practice, VBA macros are mainly used to write Droppers or Downloaders as trojans do. To trigger other stages of malware, here is the list of some of the VBA macro’s capabilities:
- Download files on the internet
- Run automatically when you open/close the document
- Create files by itself
- Execute files or commands
- Call DLL on the system to run any function
- Directly inject shellcode into Microsoft Office or to other processes
- Call any ActiveX subject
- Simulate keystrokes like the end-to-end user
There is no need to exploit anything to perform any of these listed above. They can be done by native Microsoft Office Features that have been available since 1997.
How Does VBA Stomping Works?
VBA Stomping is the process of replacing source code with fake VBA code(p-code). Because most analysis tools and antimalware engines only check the VBA source code, the malicious P-code can theoretically go undetected and run if the VBA source code is only modified to seem like something benign. This is known as VBA Stomping.
Dr. Vesselin Bontchev demonstrated VBA stomping in his VBA p-code disassembler introduction. The issue is that VBA stomping ruins the original VBA source code embedded in an Office document and compiles it into a p-code (a pseudo code for a stack machine) that can be used to spread malware. Malware document (maldoc) detection based on VBA source code is evaded in this case, and the malicious payload is successfully delivered.
You might be shocked to learn that Office will run the built VBA PerformanceCache even if the source code does not match. Microsoft doesn’t appear to have included that basic security check.
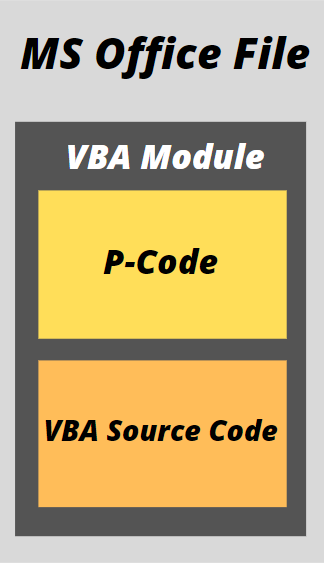
VBA Macros are stored under several forms within a document;
- VBA Source Code: Compressed plain text of the VBA Macro
- P-Code: Pre-parse bytecode, which is ready to be executed by Microsoft Office
When you open a file containing macros Microsoft Office will check this P-Code. If it matches the same version of Office, then it will directly run the P-Code without looking at the VBA source code.
The technique was first demonstrated at Derbycon 2018 by Kirk Sayre, Harold Oldgen, and Carrie Roberts with a tool called VBASeismograph.
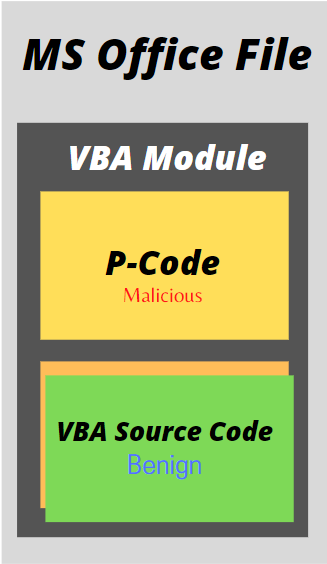
Stan Hegt published EvilClippy in 2019 to make it simple to replace malicious VBA source code with benign code. It also includes a web server that can automatically send the P-Code that matches the exact Microsoft Office version.
How to Detect VBA Stomped Files?
As long as companies use Office, Pdf, HTA, or other document types, attackers will try to sneak malicious payload into them since we have seen how VBA Stomped Microsoft Office files can be dangerous and impossible to detect in a native Microsoft environment.
Docguard’s VBA Stomping Detection
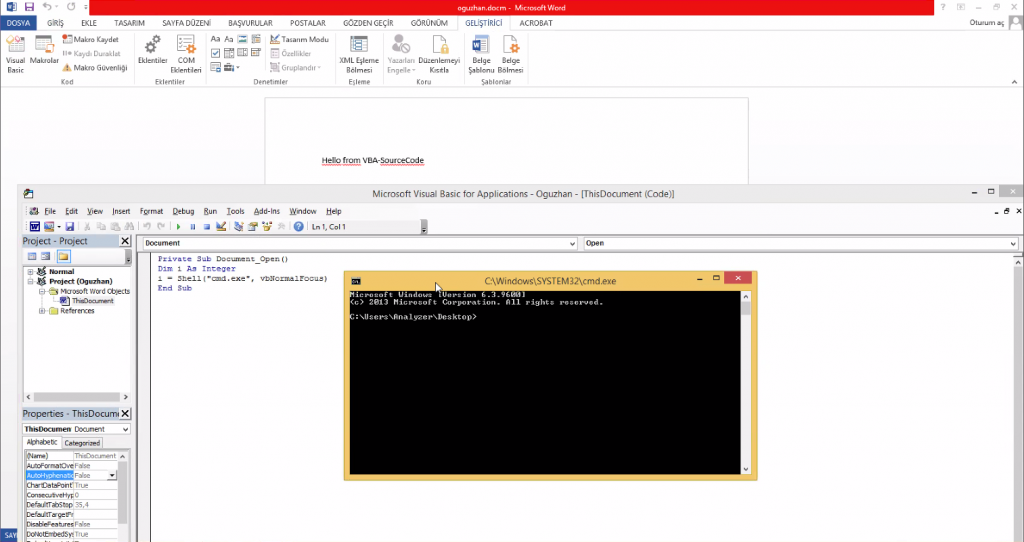
Step-1:
First, the attack macro is prepared. We make our example in Office word. Our sample macro code is malicious code that will run cmd.exe.
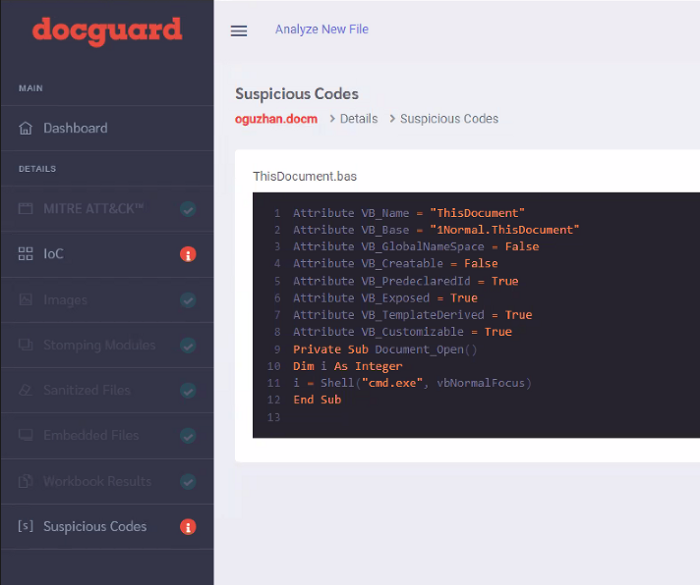
Step-2:
If we submit this document to Docguard, the VBA code is detected as malicious. We will use the VBA Stomping method to avoid getting caught in the next step.
Step-3:
We prepared a fake VBA code to show Malicious code clean. We preferred EvilClippy, one of the most famous tools for VBA Stomping.
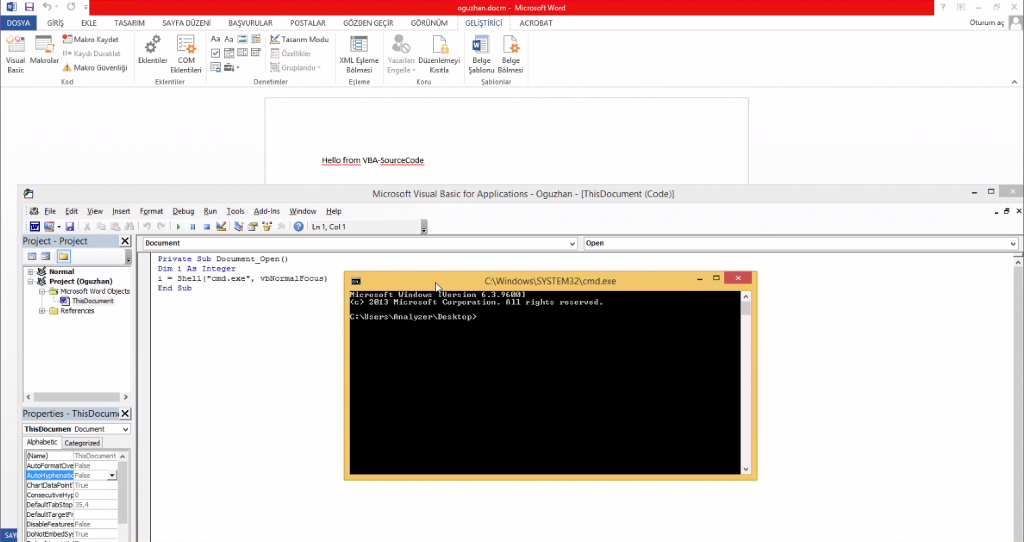
Step-4:
We upload our malicious file created with a fake code to the Docguard document analysis engine.
As a result, Docguard detects fake code.
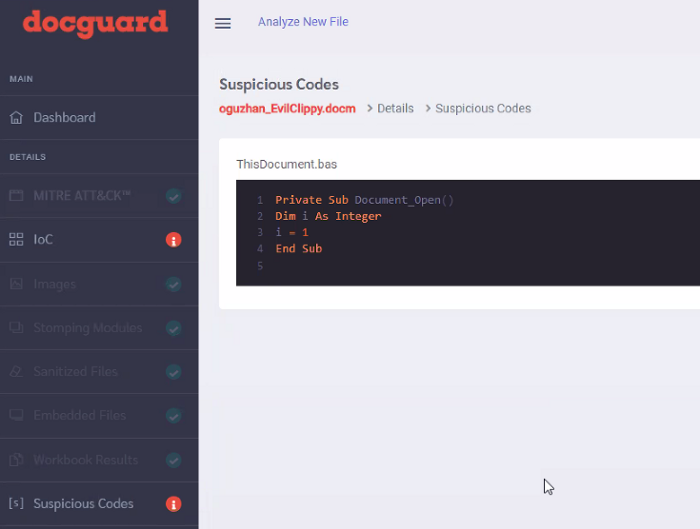
Step-5
Docguard identified that the code was stomped by detecting the P-code and VBA code differences. Unfortunately, if the analysis engine you use did not have the VBA stomping detection capability, the analysis engine would be bypassed.
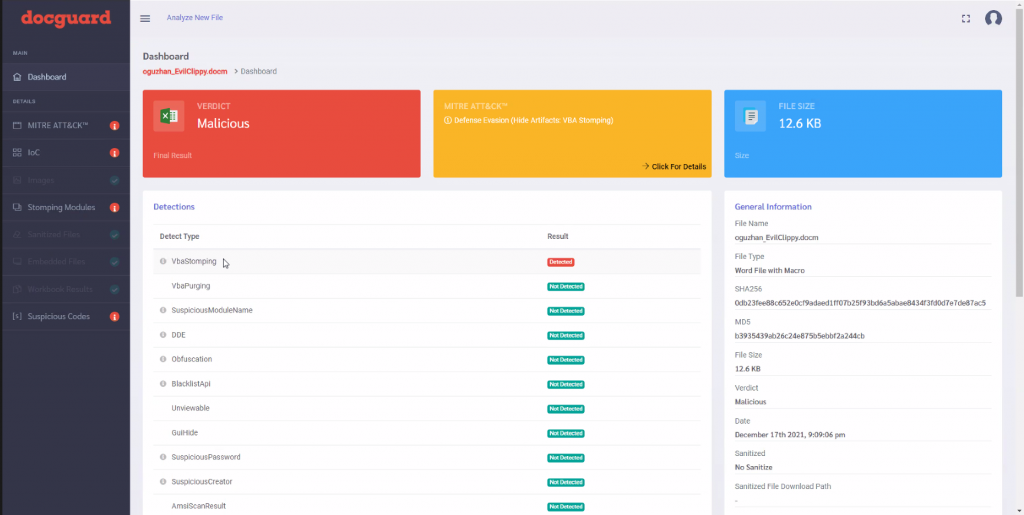
Sources
https://medium.com/walmartglobaltech/vba-stomping-advanced-maldoc-techniques-612c484ab278
https://www.decalage.info/files/eu-19-Lagadec-Advanced-VBA-Macros-Attack-And-Defence.pdf
https://office-watch.com/2020/easy-office-document-hacking-with-vba-stomping-or-purging/
https://business.blogthinkbig.com/diario-detects-stomped-macros/
https://www.fireeye.com/content/dam/fireeye-www/blog/pdfs/flareon7-challenge4-solution.pdf
https://www.opswat.com/blog/deep-cdr-prevents-advanced-maldoc-techniques-vba-stomping